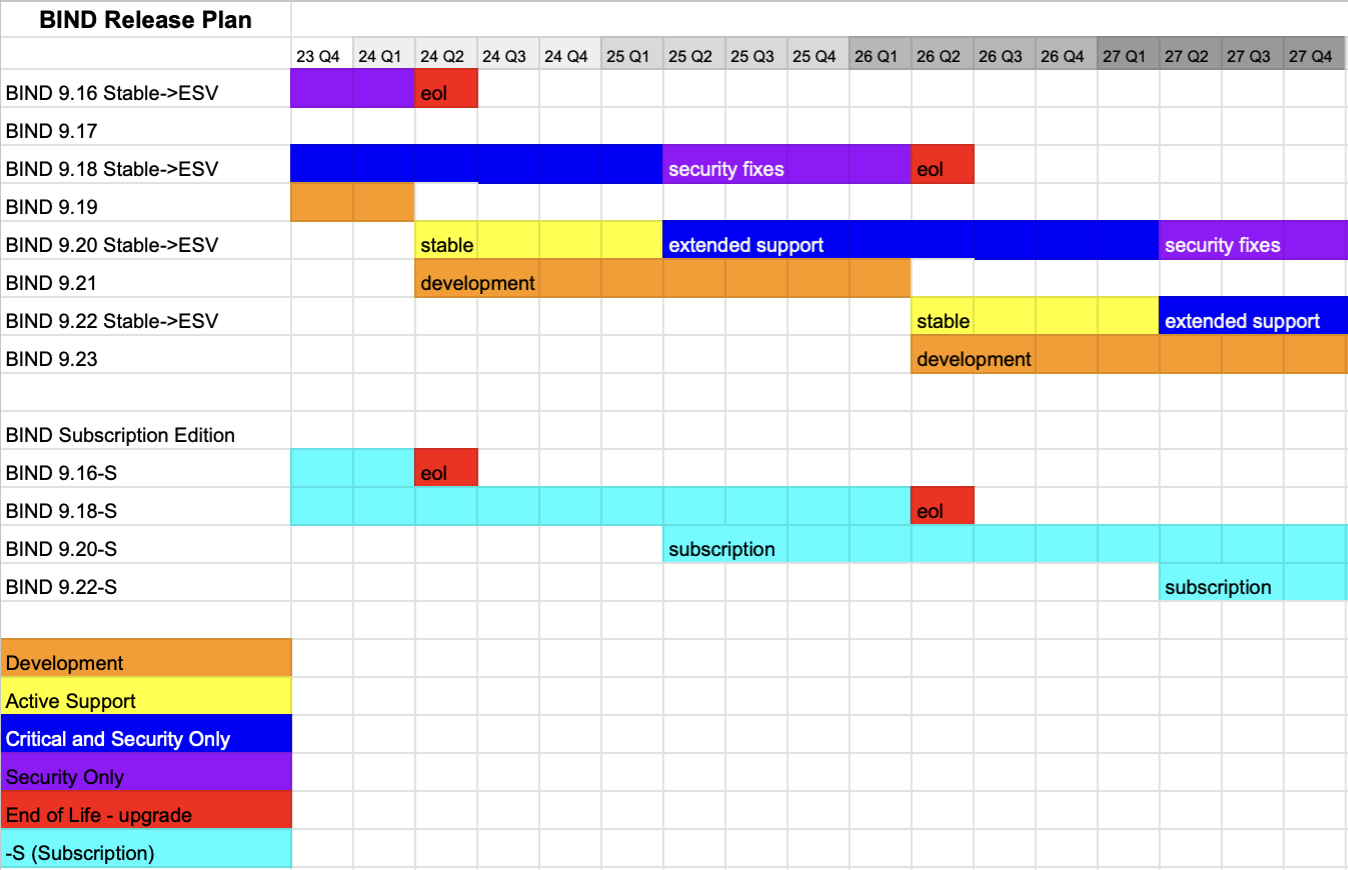
BIND 9.16 Branch is approaching EOL
The BIND 9.16 branch is approaching EOL. This branch was first published on March 6th, 2020, four years ago.
ReadVersatile, classic, complete name server software
BIND 9 has evolved to be a very flexible, full-featured DNS system. Whatever your application is, BIND 9 probably has the required features. As the first, oldest, and most commonly deployed solution, there are more network engineers who are already familiar with BIND 9 than with any other system.
BIND 9 is transparent open source, licensed under the MPL 2.0 license. Users are free to add functionality to BIND 9 and contribute back to the community through our open Gitlab.
If you want source code, download a current version from the ISC website or our FTP site. Or, install our updated ISC packages for Ubuntu, CentOS/Fedora, and the standard Debian package. If you prefer Docker, get our official Docker image.
Help is available via our community mailing list, or you may purchase a support subscription for expert, confidential, 24×7 support from the ISC team.
Contact ISC for Support

Before your mail server sends an email, before your web browser displays a web page, there is a DNS lookup to resolve a DNS name to an IP address. Watch this DNS Fundamentals presentation from Eddy Winstead of ISC or read A Warm Welcome to DNS by Bert Hubert of PowerDNS.
BIND is used successfully for every application from publishing the (DNSSEC-signed) DNS root zone and many top-level domains, to hosting providers who publish very large zone files with many small zones, to enterprises with both internal (private) and external zones, to service providers with large resolver farms.
We support three major branches of BIND 9 at a time: Stable, Extended-Support, and Development. See this advice: Which version of BIND do I want to download and install? as well as our list of supported platforms.
We also maintain a significant feature matrix and changes file.
If you would prefer a GUI management interface, you might consider a Commercial Product based on BIND.
Instructions are available for Installing and Upgrading BIND 9. ISC provides packages for Ubuntu and CentOS and Fedora and Debian - BIND 9 ESV, Debian - BIND 9 Stable, Debian - BIND 9 Development version. We also have official Docker images. Most operating systems also offer BIND 9 packages for their users. These may be built with a different set of defaults than the standard BIND 9 distribution, and some of them add a version number of their own that does not map exactly to the BIND 9 version.
The BIND Administrator Reference Manual (ARM) included in the BIND distribution is the primary reference for BIND configuration. See the Best Practices documents in our Knowledgebase for configuration recommendations.
Resolver users may find Getting started with Recursive Resolvers to be useful. There are a number of excellent books on BIND; Ron Aitchison’s DNS for Rocket Scientists is generously posted on the Internet at Zytrax.com and can be a very helpful online reference tool.
Most users will benefit from joining the bind-users mailing list. We advise all users to subscribe to bind-announce@lists.isc.org to get announcements about new versions and security vulnerabilities. For other news, see our BIND blogs.
If your DNS is critical to your business, we recommend you subscribe for technical support from ISC.
An authoritative DNS server answers requests from resolvers, using information about the domain names it is authoritative for. You can provide DNS services on the Internet by installing this software on a server and giving it information about your domain names. The BIND 9 documentation includes a description of the Primary/Secondary/Stealth Secondary roles for authoritative servers.
Response Rate Limiting (RRL) is an enhancement to named to reduce the problem of “amplification attacks” by rate-limiting DNS responses. This feature is on by default because it has proven to be so effective; it’s now even more effective with DNS Cookies, which focus rate-limiting on unknown clients. DNS cookies, per RFC 7873, are exchanged between client and server to provide IP address identity, helping to prevent attacks using forged IP addresses. Servers enforcing cookies are less susceptible to being used as an effective attack vector for DNS DDOS attacks.
Queries for ANY records are a possible abuse mechanism because they typically extract a response much larger than the query. The minimal-any option reduces the size of answers to UDP queries for type ANY by implementing one of the strategies in “draft-ietf-dnsop-refuse-any”: returning a single arbitrarily-selected RRset that matches the query name rather than returning all of the matching RRsets.
Dynamically Loadable Zones (DLZ) enable BIND 9 to retrieve zone data directly from an external database. Not recommended for high-query rate authoritative environments.
Update your BIND 9 server zone files with the remote name daemon control (rndc) utility, without restarting BIND 9. For those times when you do have to restart, the ‘map’ zone file format can dramatically speed up reloading a large zone file into BIND 9, such as on restart.
HSMs are used to store key material outside of BIND 9 for security reasons. BIND 9 supports the use of Hardware Security Modules through either a native PKCS#11 interface, or the OpenSSL PKCS#11 provider. From BIND 9.18 and beyond, only the OpenSSL PKCS#11 provider, which ISC has helped to improve, will be supported.
BIND 9 fully supports DNSSEC and has a mature, full-featured, easy-to-use implementation. Once you have initially signed your zones, BIND 9 can automatically re-sign dynamically updated records with inline signing. BIND’s Key and Signing Policy utility will help you maintain your DNSSEC implementation, periodically updating keys and signatures according to the policy you establish.
Catalog zones facilitate the provisioning of zone information across a nameserver constellation. Catalog zones are particularly useful when there is a large number of secondary servers. This feature will automatically propagate new zones added to the primary to the secondary servers, or remove zones deleted from the primary, eliminating the need for separate scripts to do this.
Dnstap is a fast, flexible method for capturing and logging DNS traffic, developed by Robert Edmonds at Farsight Security, Inc. Dnstap is supported by several open-source DNS servers, including BIND. Using dnstap enables capturing both query and response logs, with a reduced impact on the overall throughput of the BIND server than native BIND logging. Messages may be logged to a file or to a UNIX socket. Support for log-file rotation will depend on which option you choose. A utility ‘dnstap-read’ has been added to allow dnstap data to be presented in a human-readable format.
A DNS authoritative system is composed of a primary with one or more secondary servers. Zone files are established and updated on a primary server. Secondaries maintain copies of the zone files and answer queries. This configuration allows scaling the answer capacity by adding more secondaries, while zone information is maintained in only one place. The primary signals that updated information is available with a NOTIFY message to the secondaries, and the secondaries then initiate a zone transfer from the primary. BIND 9 fully supports both the AXFR (complete transfer) and IXFR (incremental transfer) methods, using the standard TSIG security mechanism between servers. There are a number of configuration options for controlling the zone updating process.
A resolver is a program that resolves questions about names by sending those questions to appropriate servers and responding to the servers’ replies. In the most common application, a web browser uses a local stub resolver library on the same computer to look up names in the DNS. That stub resolver is part of the operating system. The stub resolver usually will forward queries to a caching resolver, a server or group of servers on the network dedicated to DNS services. Those resolvers will send queries to one or multiple authoritative servers in order to find the IP address for that DNS name.
When a customer searches for a non-existent domain (NXDOMAIN response), you can redirect the user to another web page. This is done using the BIND 9 DLZ feature.
The EDNS Client Subnet feature passes a subnet address along with the DNS request, for use in selecting a customized answer. This feature is designed to help locate cached content geographically close to the client for faster response time. ISC’s ECS implementation is deployed at Quad9, among other access providers. This feature is available in the BIND 9 Subscription Edition, a premium version of BIND offered to support subscribers.
Prefetch popular records before they expire from the cache. This will improve the performance delivered to end users for resolving names that have short expiration times.
From time to time you may get incorrect or outdated records in the resolver cache. BIND 9 gives you the ability to remove them selectively or as a group.
BIND 9 is unique in providing the ability to configure different views in a single BIND server. This allows you to give internal (on-network) and external (from the Internet) users different views of your DNS data, keeping some DNS information private.
BIND 9 offers two configuration parameters, fetches-per-zone and fetches-per-server. These features enable rate-limiting queries to authoritative systems that appear to be under attack. These features have been successful in mitigating the impact of a DDoS attack on resolvers in the path of the attack.
Protect your clients from imposter sites by validating DNSSEC. In BIND 9, this is enabled with a single command. BIND 9 also has a Negative Trust Anchor feature, which temporarily disables DNSSEC validation when there is a problem with the authoritative server’s DNSSEC support. BIND 9 offers support for RFC 5011 maintenance of root key trust anchors.
A Response Policy Zone or RPZ is a specially constructed zone that specifies a policy rule set. The primary application is for blocking access to domains that are believed to be published for abusive or illegal purposes. There are companies that specialize in identifying abusive sites on the Internet, which market these lists in the form of RPZ feeds. For more information on RPZ, including a list of DNS reputation feed providers, see https://dnsrpz.info.
BIND supports QNAME minimization by default. This feature minimizes leakage of excessive detail about the query to systems that need those details. BIND will be supporting two different encryption mechanisms, DNS over HTTPS (DoH) and DNS over TLS (DoT), in BIND 9.18. These implementations are available in the development branch today.
ISC packages may be found at: CentOS Epl & Fedora, Ubuntu Launchpad, and Debian. We also have an official Docker image. Download sources here and follow these instructions to verify a download file. Note that BIND 9.18 and beyond will no longer support the native Windows(tm) operating system.
| VERSION | STATUS | DOCUMENTATION | RELEASE DATE | EOL DATE | DOWNLOAD |
|---|---|---|---|---|---|
| 9.18.26 | Current stable, ESV | BIND 9.18 ARM (
HTML
PDF
) Release Notes ( HTML ) |
April 2024 | Q2, 2026 | |
| 9.19.23 | Development | BIND 9.19 ARM (
HTML
PDF
) Release Notes ( HTML ) |
April 2024 | Q2, 2024 | |
| 9.16.50 | EOL | BIND 9.16 ARM (
HTML
PDF
) Release Notes ( HTML ) |
April 2024 | April, 2024 |
Join the bind-users mailing list to offer help to or receive advice from other users.
Join NowBefore submitting a bug report, please ensure that you are running a current version. Then, if your issue is NOT security-related, please log your report as an issue in our BIND GitLab project. If you think this bug may be a security vulnerability, please open a confidential issue in our GitLab instance (preferred) or send an email to bind-security@isc.org.
ReportTest a domain to ensure full reachability and compliance with EDNS standards.
Test| Administrator Reference Manual (ARM) | Links to current ARM on Read The Docs | |
| Binary packages | CentOS & Fedora packages from ISC, Ubuntu package from ISC | Debian -BIND9 ESV, Debian - BIND9 Stable, Debian - BIND9 Development version |
| Software version options | Supported operating systems | ISC’s Software Support Policy and Version Numbering |
| Features and versions | BIND 9 Significant Features Matrix | BIND 9 Changes file |
| Vulnerabilities | ISC Software Defect and Security Vulnerability Disclosure Policy | BIND 9 Security Vulnerability Matrix |
| Best practices | Authoritative Systems | Recursive Systems |
| DNSSEC | Additional references | |
| US Government user information | Capability statement and other references | BIND 9 Security Technical Implementation Guidelines |
| Other | DNS tools and resources | History of BIND |