Kea 3.0, our first LTS version
ISC is excited to announce the release of Kea 3.0.0! This is a major release, and is the first Long-Term Support (LTS) version of Kea.
Read postThe IETF standards community regards the possibility of pervasive monitoring as an attack on the Internet and there is strong consensus among IETF participants that we must protect Internet users’ privacy.
We were wondering whether the people who are operating DNS services were feeling a similar sense of urgency, and if they had any significant concerns about obstacles to deployment.
From March 25 – May 4, 2018, we ran a survey, advertised via social media and ISC’s Software Downloads page, asking whether people running DNS systems were interested in deploying DNS privacy, and what concerns they had.
Here are the results of that survey.
We advertised on social media, but then worried that most of those respondents might be specifically interested in privacy, so we added a survey invite on ISC’s Software Downloads page to get participation from people who might not follow ISC on social media. There was no “prize” offered for completing the survey and no recognition, so the only likely motivation was wanting to help us out.
We got 195 responses in total.
With an open survey like this, there is no real way to ensure that the respondents are representative of the overall operator population. We asked only the minimum of demographic questions to keep the survey very short, to maximize completion of the survey. We did not collect any personally-identifying information. (It’s a privacy survey!)
| Answer choice | Percentage of total respondents |
|---|---|
| Individual consumer, Internet user | 23% |
| Internet Service Provider (access + services) | 18% |
|
Educational organization |
12% |
|
In the business of creating products that leverage the Internet |
10% |
|
Internet-enabled business |
9% |
|
Enterprise (not primarily dependent on the Internet) |
8% |
|
Hosted (cloud) services provider |
5% |
|
Government office |
3% |
| Other* | 11% |
We asked those who selected “Other” what their role was, and the responses mostly indicated an individual contributor, rather than service operator role. Responses included: consultant, hobbyist, small business, Internet engineer, registrar.
Although the largest number of responses came from the United States, 50 countries were represented, including countries in South America, the Middle East, the Caribbean, and Africa. Participation was relatively weaker across Asia, outside of China.
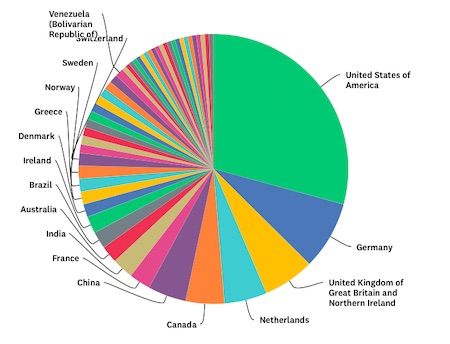
For a read-only view of the charts on Survey Monkey, click here.
If we develop QNAME minimization in BIND, we can expect that approximately half our users are open to deploying it. That seems like a good level of commitment for a feature that isn’t even developed yet. (QNAME minimization is currently in development in BIND. Unbound has already released support for this feature.) Since some respondents are already using QNAME minimization, we can infer that not all respondents are BIND users. As one respondent pointed out to us, DNSdist has QNAME minimization but the PowerDNS Recursor does not.
Interest in QNAME minimization was somewhat lower among individual contributors than service operators. The reason for this is not obvious from this survey.
For privacy advocates, the fact that 50% see a marketing benefit in touting privacy protections is an opportunity. Perhaps we need a “DNS Privacy Compliant” sticker for services?
We might have gotten more useful insights if we had qualified respondents more, selecting only those running recursive services, and asking how many end users their services supported. Since DNS Privacy really only applies to recursive services, the authoritative operators and registrars who answered the survey may have been confused about how to answer and may have obscured the trends among resolver operators.
There was no consensus about what GDPR might mean for DNS operators.
To find out more about what DNS Privacy means, we recommend the website for the DNS Privacy Project.
I am willing to share the whole data set with anyone – there is no personally-identifying information in it. If you would like the data dump, please email me at vicky at isc dot org.
What's New from ISC