Kea 3.0, our first LTS version
ISC is excited to announce the release of Kea 3.0.0! This is a major release, and is the first Long-Term Support (LTS) version of Kea.
Read postISC is delighted to announce the release of Stork 0.11. This is a development release of the Stork dashboard for Kea. Note that we recently released a new version of Kea, Kea 1.6.3 which adds the api call required for monitoring with Stork, so you can now use Stork with Kea 1.6. Stork also works with Kea 1.7.x versions.
This is somewhat smaller release than usual. Some team members enjoyed a well-earned vacation this month, and those that were in the office focused on pushing a major release of Kea 1.8.0 out the door. With the summer holiday period coming to a close and the full team back in the office, we expect the next Stork release to be a bit bigger.
The notable new features, bug fixes and changes introduced in this version are:
Security improvements. For the last couple of months, Stork has been adding many new features in each release. This time, we are focusing on security improvements. Many dependencies have been updated to their latest versions without any known vulnerabilities (#362), the credentials are now passed in a more secure way that is not susceptible to data leakage in proxy logs (#375), and the sanity checks for the log viewer capability are now vastly improved (#348).
UI improvements. The status of BIND 9 daemons is now displayed correctly (#379), and the tables are displayed better on low-resolution (720p) devices (#295). Also, the dashboard no longer shows daemons that are not monitored (#365).
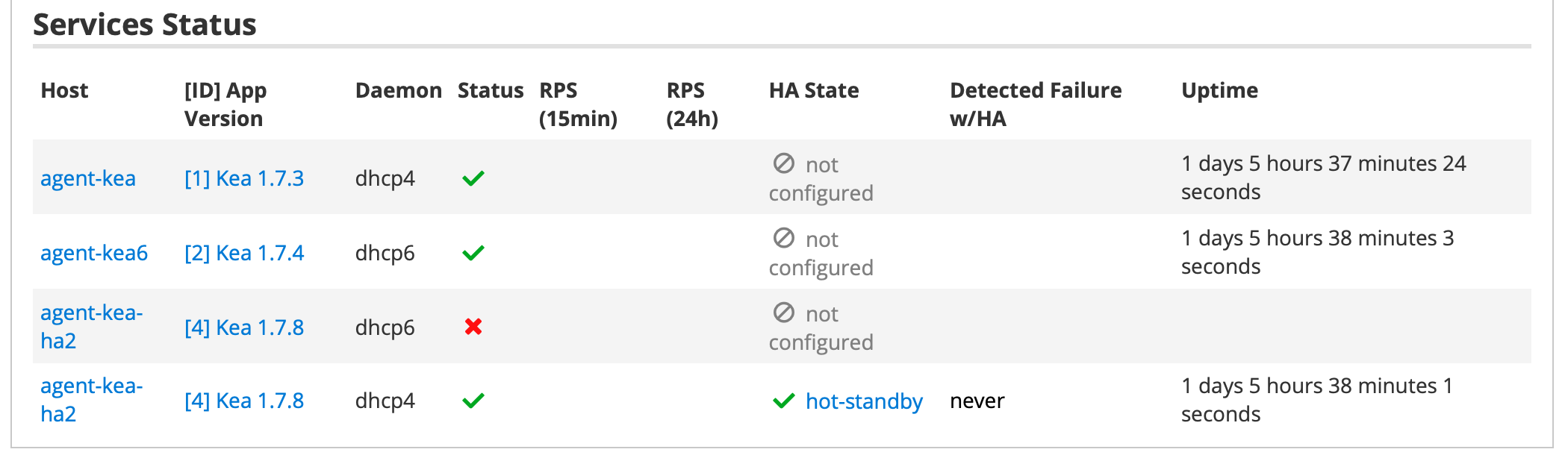 Stork 0.11 Services Display
Stork 0.11 Services Display
Documentation. The section explaining how to use the Stork agent as a Prometheus exporter for BIND 9 was expanded (#382).
Bug fixes. Stork no longer gets confused when the database access password uses uppercase letters (#361), and the daemon status is now presented correctly after recovering from a connection breakdown (#384).
Stork Environment Simulator. Running Stork demo is a popular way to get your first experience with Stork. There are two separate pages, DHCP Traffic Generator and DNS Traffic Generator. Those two tools were merged and evolved into the Stork Environment Simulator. You can add all of the predefined demo machines to your demo Stork server with a single click. This tool was extended in this release to add the ability to simulate Kea failures by stopping and starting services. This is useful for experimenting with the monitoring of Kea High Availability pairs. (#380).
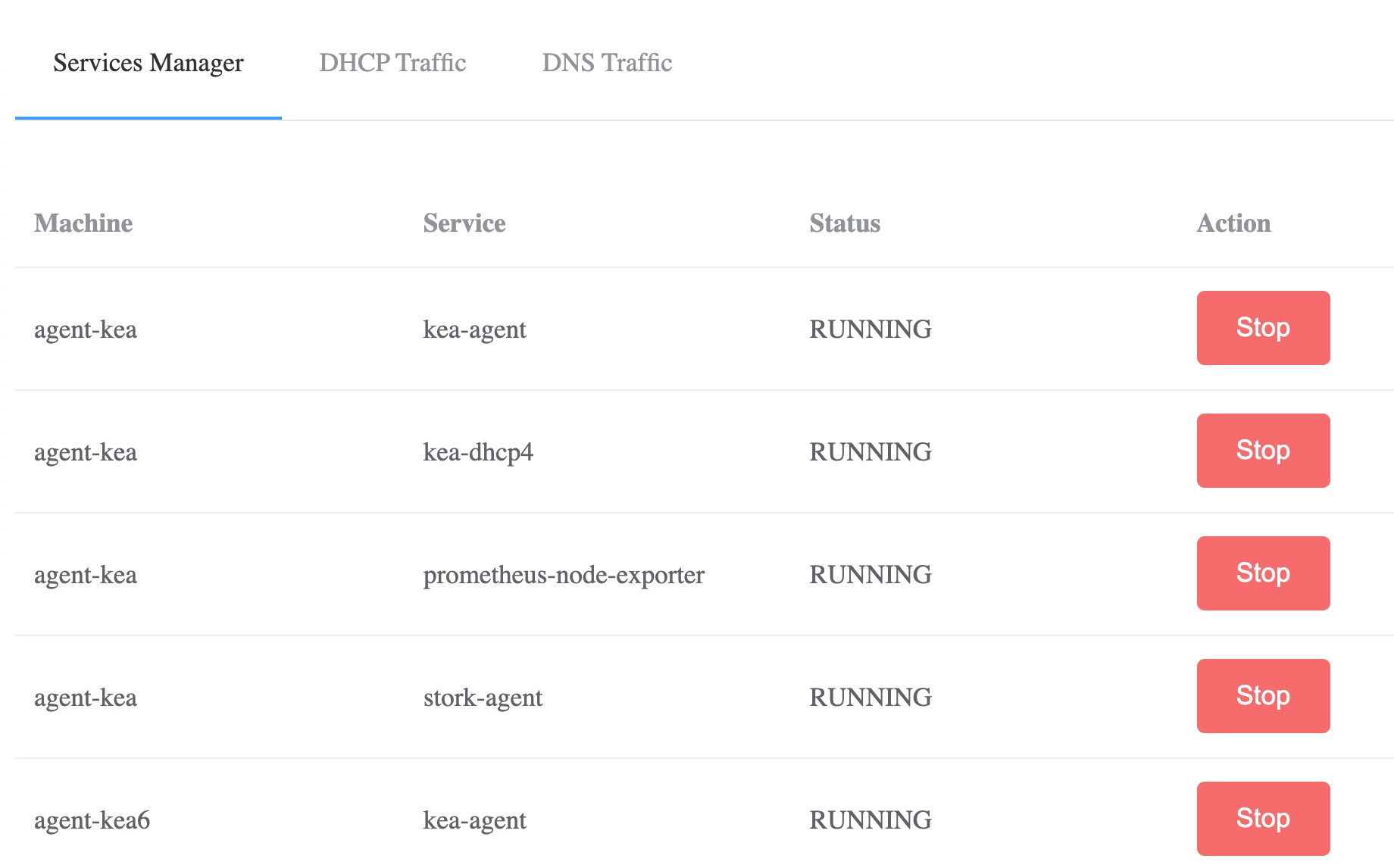 Stork 0.11 Environment Simulator can simulate Kea server failures
Stork 0.11 Environment Simulator can simulate Kea server failures
This version of Stork is released under the Mozilla Public License, version 2.0.
The easiest way to install the software is to use native deb or RPM packages. They can be downloaded from our open source package repository on Cloudsmith.
The Stork source and PGP signature for this release may be downloaded from: https://downloads.isc.org/isc/stork The signature was generated with the ISC code signing key.
ISC provides documentation in the Stork Administrator Reference Manual. It is available on ReadTheDocs.io, and in source form in the docs/ directory. We ask users of this software to please let us know how it worked for you and what operating system you tested on. Feel free to share your feedback on the stork-users mailing list. We would also like to hear whether the documentation is adequate and accurate. Please open tickets in the Stork GitLab project for bugs, documentation omissions and errors, and enhancement requests. We want to hear from you even if everything worked.
Professional support for Stork will become available once it reaches the 1.0 milestone. Existing ISC customers that consider themselves very early adopters may get involved in the development process, including roadmap, features planning, and early testing, but the software maturity level does not constitute a typical professional service before the 1.0 milestone. Free best-effort support is provided by our user community via the user mailing list. Information on all ISC public email lists is available. If you have any comments or questions about working with Stork, please share them to the stork-users list. Bugs and feature requests may be submitted via GitLab.
The following summarizes changes and important upgrades since the Stork 0.10.0 release. This text references issue numbers. For more details, visit the Stork GitLab page.
* 101 [func] godfryd
Merged Stork DHCP Traffic Simulator and Stork DNS Traffic
Simulator into one web application called Stork Environment
Simulator. Added there capabilities for adding all present
machines in demo setup and ability to stop and start Stork Agents,
Kea and BIND 9 daemons. This allows simulation of communication
issues between applications, Stork Agents and Stork Server.
(Gitlab #380)
* 101 [func] marcin
Restrict log viewer's access to the remote files. The log viewer
can only access log files belonging to the monitored application.
(Gitlab #348)
* 100 [func] godfryd
Improved user experience of updating machine address/port.
Improved visual aspects. Added refreshing state from the machine
after changing the address.
(Gitlab #283)
* 99 [func] godfryd
The DHCP dashboard now is presenting only monitored daemons.
The daemons that have monitoring switched off are not visible
in the dashboard.
(Gitlab #365)
* 98 [bug] marcin
Corrected an issue causing false errors about broken communication
with the monitored Kea application after the application was
brought back online.
(Gitlab #384)
* 97 [bug] godfryd
Improved layout of various tables that they are displayed
correctly
on smaller screens. Fixed address of the machine that is displayed
in the tables (previous it was always showing 127.0.0.1).
(Gitlab #295)
* 96 [doc] matthijs
Add documentation on monitoring the BIND 9 application.
(Gitlab #382)
* 95 [func] godfryd
Fixed presenting an application status on a machine tab
with BIND 9 application. Previously it was always red/inactive.
Now it is presented the same way as it is for Kea app: status
per each daemon of an app.
(Gitlab #379)
* 94 [bug] marcin
Fixed an issue whereby the user was unable to login to Stork
when database password conatined upper case letters. In addition,
passwords with spaces and quotes are now also supported.
(Gitlab #361)
* 93 [func] marcin
Login credentials are passed in the message body rather than as
query parameters. In addition, the user information is obfuscated
when db tracing is enabled.
(Gitlab #375)
Thank you again to everyone who assisted us in making this release possible.
What's New from ISC